Awareness - 8 July 2022
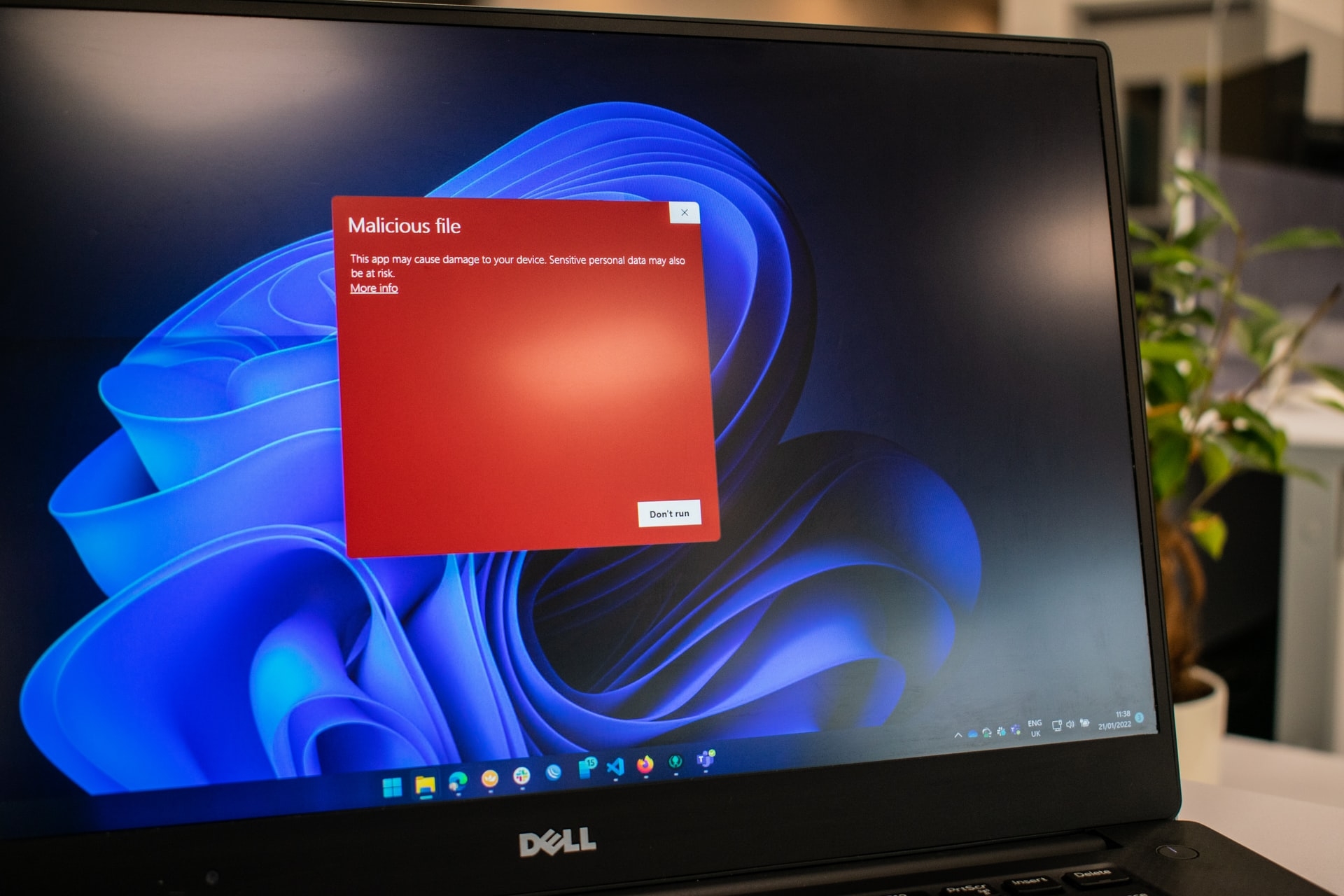
Antivirus, obsolete technology or still relevant?
All means are good for a computer virus to infect you: by surfing on the Internet, by clicking on a link, by downloading and executing an attachment, by plugging a hard disk or a USB key... Is it necessary to install an antivirus to protect yourself? Is it enough? What is a virus and how does it spread? Viruses can take any form. Ransomware, Trojan horses, spyware, these malicious computer programs have a single objective: to disrupt the normal functioning of a computer system without the…